用python做一个能过360的免杀CS马
目录
# [用python做一个能过360的免杀CS马](https://ybrc.github.io/zh-cn/11)
拿到shell了, 机器上有个360?? 做个免杀吧!
更新: python真的不行…还是老老实实C++写吧 (
本文将通过python的ctypes库加载Cobalt Strike马实现免杀.
其实这已经不是一个新方法了; 但是它依然十分有效, 即使不做任何混淆也能过360.
写个python文件加载CS shellcode
shellcode写到内存中, 用ctypes.windll加载即可.
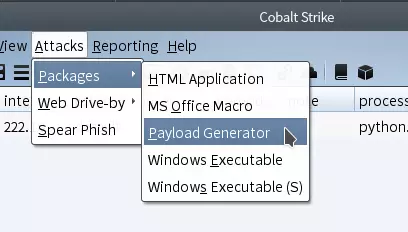
先用CS生成shellcode, Output类型选python
然后放进这份网传的python代码中, 替换掉buf.
|
|
Python
记得全程用python2. python3.9因未知原因失败了.
它运行一下就可以CS上线了.
混淆/编码
不编码也能过360, 不过还是编码一下比较保险一些.
你可以尝试:
- 编码shellcode
- 编码整个程序然后exec
- etc…
可以对每个byte异或一个字符, 或者上加密.
用PyInstaller打包成exe
很简单,
|
|
Shell
即可.
注意: 如果你编码了程序, 记得在最外层import所有需要的库, 否则执行时会因为找不到库而出错.
不要在联网状态下扫描你的程序, 不然第二天它就挂了(
是这样… 第二天挂了之后, 再尝试换个花样上去几分钟就被360杀了, 可能360记录了我的ip之类的. 考虑上cloudflare转发?